FSM Ingress Controller
Kubernetes Ingress Controller implementation provided by FSM
The Kubernetes Ingress API is designed with a separation of concerns, where the Ingress implementation provides an entry feature infrastructure managed by operations staff; it also allows application owners to control the routing of requests to the backend through rules.
Ingress is an API object for managing external access to services in a cluster, with typical access through HTTP. It provides load balancing, SSL termination, and name-based virtual hosting. For the Ingress resource to work, the cluster must have a running Ingress controller.
Ingress controller configures the HTTP load balancer by monitoring Ingress resources in the cluster.
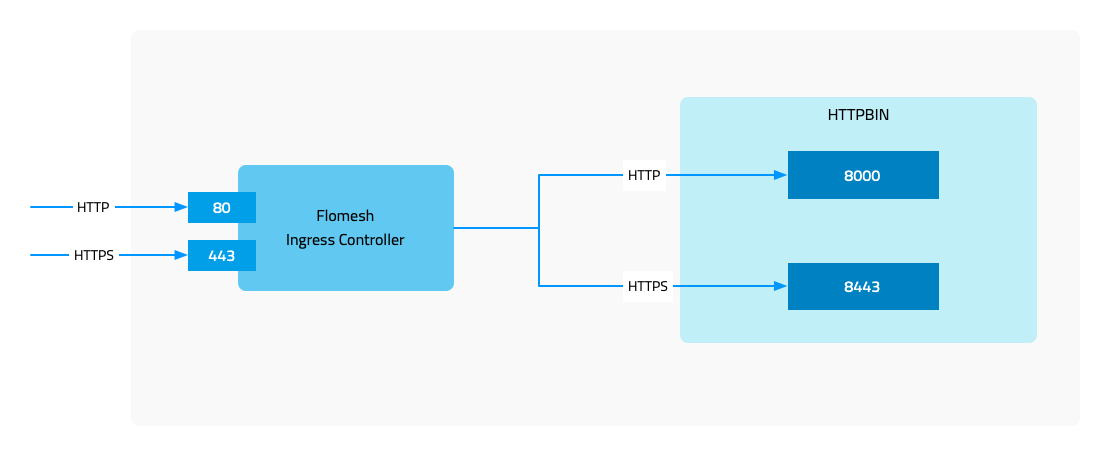
1 - Installation
Enable Ingress Controller in cluster
Installation
Prerequisites
- Kubernetes cluster version v1.19.0 or higher.
- FSM version >= v1.1.0.
- FSM CLI to install FSM and enable FSM Ingress.
There are two options to install FSM Ingress Controller. One is installing it along with FSM during FSM installation. It won’t be enabled by default so we need to enable it explicitly:
fsm install \
--set=fsm.fsmIngress.enabled=true
Another is installing it separately if you already have FSM mesh installed.
Using the fsm command line tool to enable FSM Ingress Controller.
Check the resource.
kubectl get pod,svc -n fsm-system -l app=fsm-ingress
NAME READY STATUS RESTARTS AGE
pod/fsm-ingress-574465b678-xj8l6 1/1 Running 0 14h
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/fsm-ingress LoadBalancer 10.43.243.124 10.0.2.4 80:30508/TCP 14h
Once all done, we can start to play with FSM Ingress Controller.
2 - Basics
Guide on basics of FSM Ingress basics
Demo
3 - Advanced TLS
Guide on configuring FSM Ingress with TLS and its advanced use
FSM Ingress Controller - Advanced TLS
In the document of FSM Ingress Controller, we introduced FSM Ingress and some of its basic functinoality. In this part of series, we will continue on where we left and look into advanced TLS features and we can configure FSM Ingress to use them.
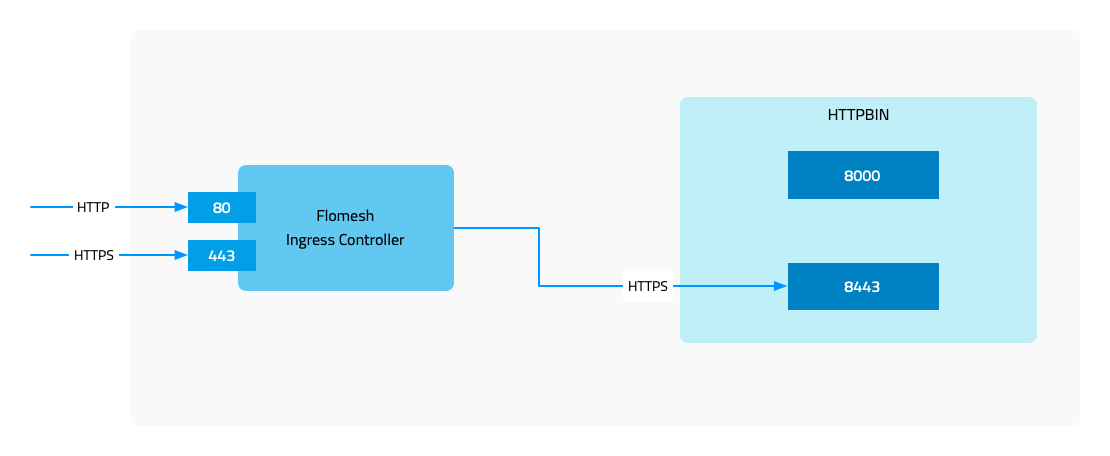
Normally, we see below four combinations of communication with upstream services
- Client -> HTTP Ingress -> HTTP Upstream
- Client -> HTTPS Ingress -> HTTP Upstream
- Client -> HTTP Ingress -> HTTPS Upstream
- Client -> HTTPS Ingress -> HTTPS Upstream
Two of the above combinations has been covered in basics introduction blog post and in this article we will introduce the remaining two combinations i.e. communicating with an upstream HTTPS service.
- HTTPS Upstream: The certificate of the backend service, the upstream, must be checked.
- Client Verification: Mainly when using HTTPS entrance, the certificate used by the client is checked.
Demo
4 - TLS Passthrough
Guide on configuring TLS offloading/termination, passthrough on FSM Ingress
FSM Ingress Controller - TLS Passthrough
This guide will demonstrate TLS passthrough feature of FSM Ingress.
What is TLS passthrough
TLS (Secure Socket Layer), also known as TLS (Transport Layer Security), protects the security communication between the client and the server through encryption.
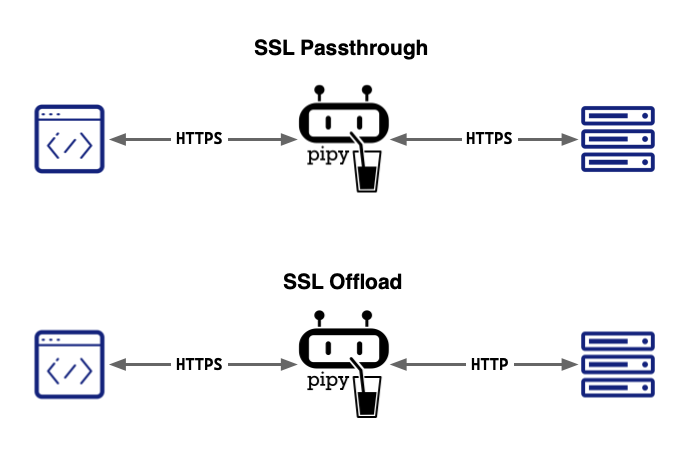
TLS Passthrough is one of the two ways that a proxy server handles TLS requests (the other is TLS offload). In TLS passthrough mode, the proxy does not decrypt the TLS request from the client but instead forwards it to the upstream server for decryption, meaning the data remains encrypted while passing through the proxy, thus ensuring the security of important and sensitive data.
Advantages of TLS passthrough
- Since the data is not decrypted on the proxy but is forwarded to the upstream server in an encrypted manner, the data is protected from network attacks.
- Encrypted data arrives at the upstream server without decryption, ensuring the confidentiality of the data.
- This is also the simplest method of configuring TLS for the proxy.
Disadvantages of TLS passthrough
- Malicious code may be present in the traffic, which will directly reach the backend server.
- In the TLS passthrough process, switching servers is not possible.
- Layer-7 traffic processing cannot be performed.
Installation
The TLS passthrough feature can be enabled during installation of FSM.
fsm install --set=fsm.image.registry=addozhang --set=fsm.image.tag=latest-main --set=fsm.fsmIngress.enabled=true --set=fsm.fsmIngress.tls.enabled=true --set=fsm.fsmIngress.tls.sslPassthrough.enabled=true
Or you can enable it during FSM Ingress enabling when already have FSM installed.
fsm ingress enable --tls-enable --passthrough-enable
Demo


